Analysis | The rise of ransomware: how data extortion became the biggest thing in cybercrime
A recent outbreak of ransomware attacks, from the WannaCry worm in May to Tuesday’s infection of thousands of computer systems around the globe, shows that digital stickups are becoming the go-to hack for cybercriminals, fueled by powerful leaked US government tools and the rise of bitcoin and other anonymous digital currencies.
Tuesday’s attack showed no signs of slowing down, as cybersecurity researchers had not found a kill switch similar to the one that allowed them to stop WannaCry after it had infected hundreds of thousands of computer in more than 150 countries, preventing it from becoming one of the worst attacks on record.

The new versions of ransomware are the perfect crime
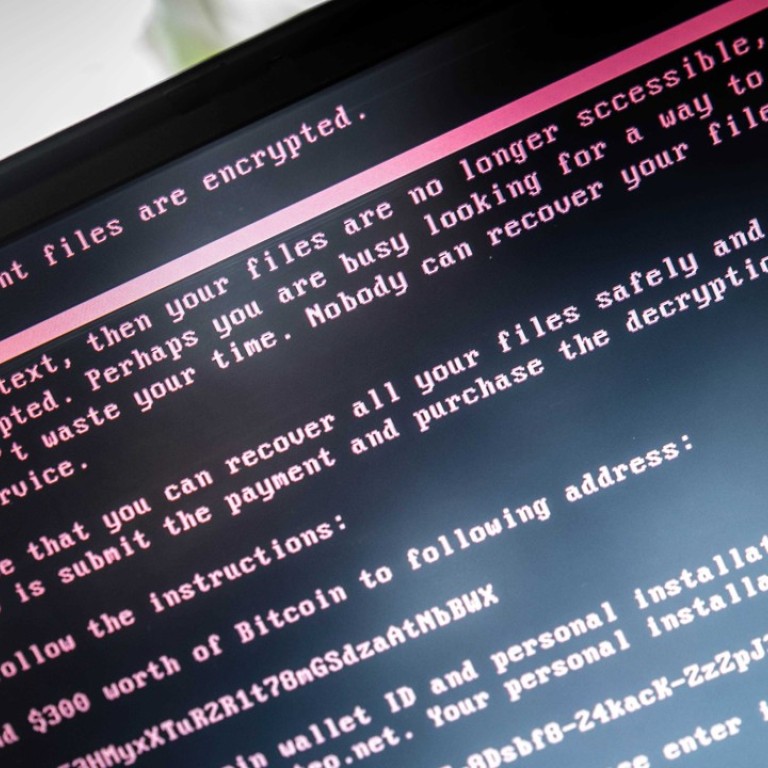
Banks and retailers have strengthened their defences, driving the price for stolen credit card numbers down to as little as 50 cents apiece, according to research from Symantec Corp, the biggest cybersecurity software maker. But ransomware demands are on the rise, nearly tripling from an average of about US$300 per computer infected in 2015 to more than US$1,000 each last year, Symantec said. Earlier this month, a South Korean web hosting company agreed to pay more than US$1 million to unlock its servers in what’s believed to be the biggest ransomware payout on record.
“The new versions of ransomware are the perfect crime,” said Jack Danahy, co-founder of Barkly Protects Inc., a Boston-based cybersecurity firm. “It’s super-easy to do - monkeys could do it - and the profits are remarkably high. And the third thing that makes it perfect is anonymity, because nobody wants to get caught. That’s why this thing is growing.”

The new malware does have additional capabilities that let it spread by other means through internal networks, so anyone who clicks on a malicious email attachment could put their entire organization at risk.
The rise of ransomware has coincided with two other major changes in the cyber black market. The first is the growing amount of leaked attack tools from the US government available online. The second is the growing use of digital currencies, which give hackers an easy and potentially anonymous way to get paid. The malware unleashed Tuesday demands payment of US$300 in bitcoin. The reason many ransomware operators ask for relatively small payments is that the amount needs to be low enough that enough people will pay, but high enough that it’s worth the effort to attack. Given the secretive nature of cryptocurrencies and the shadowy world in which cybercriminals operate, it’s virtually impossible to get an accurate read on exactly how much the hackers rake in.
Because there’s a glut of credit card and identity data for sale on the black market, it’s gotten harder for criminals to get paid, said Jeremiah Grossman, chief of security strategy for SentinelOne. But rather than try to sell data to a third party, attackers instead encrypt it - demanding that the victim pay to get it back.
“Who better to value the data than the owner of the data?” Grossman said. “It’s market forces at work.”
There are signs that hackers are shifting tactics in favour of ransomware. According to a study by IBM, the amount of spam containing ransomware surged to 40 per cent by the end of 2016 from just 0.6 per cent in 2015. While many ransomware attacks are blocked by security software, the number of infections getting through is growing. Symantec said it detected 463,000 ransomware infections in 2016, 36 per cent higher than the year before.

