National Security Agency seeks to break into Tor anonymous network
Tor, used by businesses, media, activists and militants worldwide to hide their identities, is target of spy agency, Snowden documents show
On November 1, 2007, the US National Security Agency hosted a talk by Roger Dingledine, principal designer of one of the world's leading internet privacy tools.

According to a top-secret NSA summary of the meeting, Dingledine told the assembled NSA staff that his service, called Tor, offered anonymity to people who needed it badly. They wanted this, he said, to keep business secrets, protect their identities from oppressive political regimes or conduct research without revealing themselves.
But in the minds of NSA officials, Tor was offering protection to terrorists and other intelligence targets.
As he spoke to the NSA, Dingledine said in an interview on Friday, he suspected the agency was attempting to break into Tor, which is used by millions of people around the world to shield their identities.
Documents provided by former agency contractor Edward Snowden show he was right.
Beginning at least a year before Dingledine's visit, the NSA mounted increasingly successful attacks to unmask the identities and locations of Tor users. In some cases, the agency has succeeded in blocking access to the anonymous network, diverting Tor users to insecure channels. In others, it has been able to "stain" anonymous traffic as it enters the Tor network, enabling the NSA to identify users as it exits.
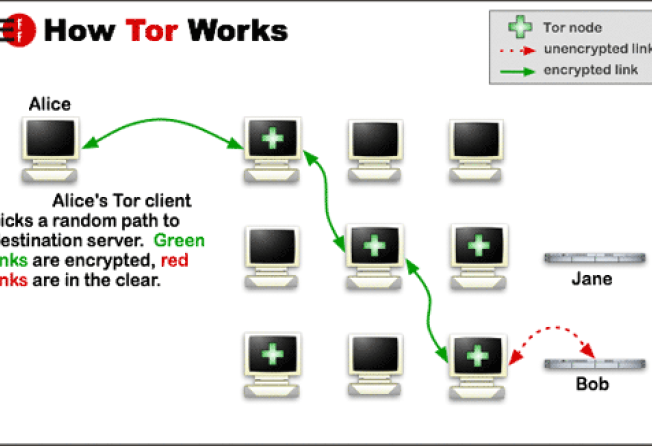
Tor works by encrypting traffic repeatedly as it flows across a global network of servers, mostly run by volunteers. The traffic, which can include e-mails, information from a website and almost anything else on the internet, is supposed to arrive at its destination with no identifying information about its origin or the path it took.
It is relied on by journalists, activists and campaigners in the US and Europe as well as in China, Iran and Syria to maintain the privacy of their communications and avoid reprisals from government. China has tried on multiple occasions to block Tor entirely.
The Snowden documents suggest that the NSA cannot see directly inside Tor's anonymous network but that it has repeatedly uncloaked users by circumventing Tor's protections. The documents also illustrate the power of the NSA to at least partially penetrate what have long been considered the most secure corners of the internet.
The US Naval Research Laboratory first developed Tor more than a decade ago. It continues to receive substantial US federal funding. Tor is now maintained by Dingledine's non-profit group, the Tor Project.
The US State Department trains political activists worldwide on how to use Tor to protect communications from the intelligence services of repressive governments. But the anonymity service also has become popular with criminals and terrorists.
One of the documents provided by Snowden said an NSA technique code-named EGOTISTICALGIRAFFE had succeeded in unmasking 24 Tor users in a single weekend. The same operation allowed the NSA to discover the identity of a key propagandist for al-Qaeda in the Arabian peninsula after he posted information and instructions on the group's website.
In a statement, Director of National Intelligence James Clapper said the intelligence community "seeks to understand" tools that facilitate anonymous communication. He added that it did so because of the "undeniable fact that these are the tools our adversaries use to communicate and co-ordinate attacks against the United States and our allies".
There is no evidence that the NSA is capable of unmasking Tor traffic routinely. But for almost seven years, it has been trying.
In the interview, Dingledine said the weaknesses in Tor described in the documents could probably be exploited only against a relatively small number of individual users. That, he said, is reassuring.
"If those documents actually represent what they can do, they are not as big an adversary as I thought," he said.