Why China’s universities are so vulnerable to WannaCry global cyberattack
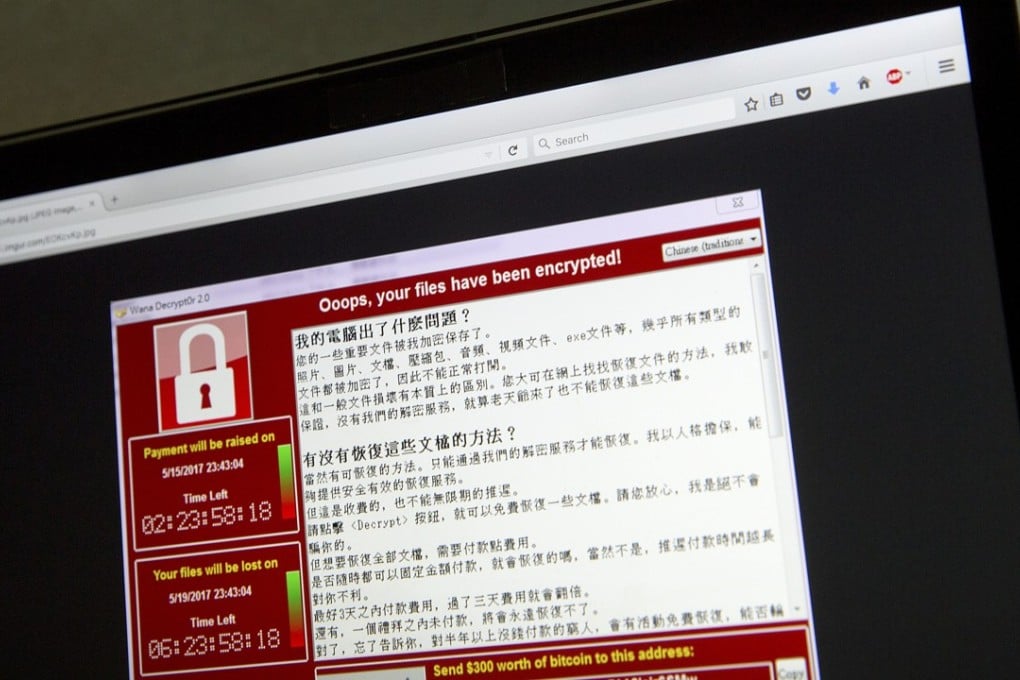
As the global fallout from a massive cyberattack ebbed on Tuesday, it emerged that universities bore the brunt of the assault in China – even as Chinese authorities contested the extent of the damage.
More than 4,300 Chinese educational institutions were infected by the WannaCry ransomware that spread across the globe last Friday, according to Chinese cybersecurity giant Qihoo 360’s Threat Intelligence Centre. Almost 30,000 organisations across the country were affected in all.
But the Ministry of Education’s China Education and Research Network (Cernet) said just 66 out of 1,600 Chinese universities were affected, rejecting reports of widespread damage in higher-education computer systems as “malicious” hype.
Cernet said the 66 universities were affected mainly because their operating systems were not regularly upgraded rather than any major security shortcomings.
It dismissed Qihoo 360’s claims as “inaccurate statements that have seriously misled public opinion, caused panic among teachers and students, and affected the normal order of instruction and life”.