
The next ransomware attack will likely be worse than WannaCry warns security tech and author
The most recent cyberattack affected more than 230,000 computers around the world, but what will happen when the Internet of Things is targeted?
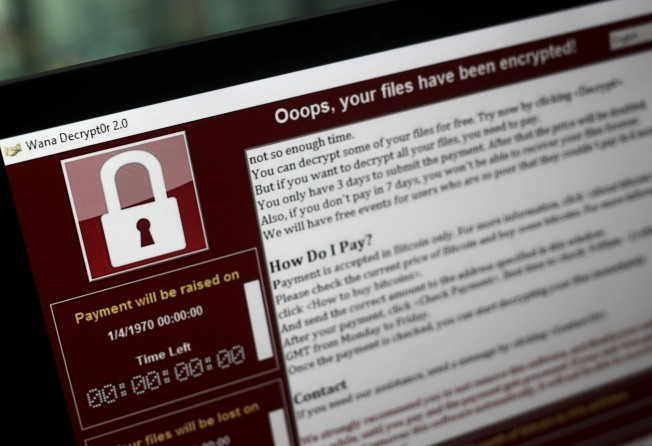
Ransomware isn’t new, but it’s increasingly popular and profitable.
The concept is simple. Your computer is infected with a virus that encrypts your files until you pay a ransom.

WannaCry is the latest headline-making ransomware that has affected computer systems in more than 150 countries and cities including Hong Kong. At least 30 local cases were reported last week to have been infected by the virus, according to the Hong Kong Computer Emergency Response Team. China was hit harder, with 30,000 organisations reportedly affected.
WannaCry doesn’t seem to be any more virulent or more expensive than other ransomware.
But it does have an interesting pedigree. It’s based on a vulnerability developed by the National Security Agency that can be used against many versions of the Windows operating system. The NSA’s code was, in turn, stolen by an unknown hacker group called Shadow Brokers – widely believed by the security community to be Russian – in 2014 and released to the public in April.
Microsoft patched the vulnerability a month before, presumably after being alerted by the NSA that the leak was imminent. But the vulnerability affected older versions of Windows that Microsoft no longer supports, and there are still many people and organisations that don’t regularly patch their systems. This allowed whoever wrote WannaCry – it could be anyone from a lone individual to an organised crime syndicate – to use it to infect computers and extort users.
The lessons for users are obvious: keep your system patches up to date and back up your data regularly. This isn’t just good advice to defend against ransomware, but good advice in general. But it’s becoming obsolete.

Everything is becoming a computer. Your microwave is a computer that makes things hot. Your refrigerator is a computer that keeps things cold. Your car and television, the traffic lights and signals in your city and national power grid are all computers. This is the much-hyped Internet of Things. It’s coming, and faster than you might think. And as these devices connect to the internet, they become vulnerable to ransomware and other computer threats.
It’s only a matter of time before people get messages on their car screens saying that the engine has been disabled and it will cost US$200 in bitcoin to turn it back on. Or a similar message on their phones about their internet-enabled door lock telling them to pay US$100 if their want to get into their house tonight. Or pay far more if they want their embedded heart defibrillator to keep working.
This isn’t just theoretical. Researchers have already demonstrated a ransomware attack against smart thermostats, which may sound like a nuisance at first but can cause serious property damage if it’s cold enough outside. If the device under attack has no screen, you’ll get the message on the smartphone app you control it from.
Hackers don’t even have to come up with these ideas on their own; the government agencies whose code was stolen were already doing it. One of the leaked CIA attack tools targets internet-enabled Samsung smart televisions.
Even worse, the usual solutions won’t work with these embedded systems. You have no way to back up your refrigerator’s software, and it’s unclear whether that solution would even work if an attack targets the functionality of the device rather than its stored data.
These devices will be around for a long time. Unlike our phones and computers, which we replace every few years, cars are expected to last at least a decade. We want our appliances to run for 20 years or more, our thermostats even longer.
What happens when the company that made our smart washing machine – or just the computer part – goes out of business, or otherwise decides that they can no longer support older models?

That won’t happen with low-cost internet-of-things devices.
Those devices are built on the cheap, and the companies that make them don’t have the dedicated teams of security engineers ready to craft and distribute security patches. The economics doesn’t allow for it. Even worse, many of these devices aren’t patchable.
Remember last autumn when the Murai botnet infected hundreds of thousands of internet-enabled digital video recorders, webcams and other devices and launched a massive denial-of-service attack that resulted in a host of popular websites dropping off the web? Most of those devices couldn’t be fixed with new software once they were attacked. The way you update your DVR is to throw it away and buy a new one.

We need to assign liabilities to companies that write insecure software that harms people, and possibly even issue and enforce regulations that require companies to maintain software systems throughout their life cycle. We may need minimum security standards for critical devices.
And it would help, in the US, if the NSA got more involved in securing our information infrastructure and less in keeping it vulnerable so the government can eavesdrop.
I know this all sounds politically impossible right now, but we simply cannot live in a future where everything – from the things we own to our nation’s infrastructure – can be held for ransom by criminals again and again.
The Washington Post
Schneier is a security technologist and a lecturer at the Kennedy School of Government at Harvard University. His latest book is Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World.