
‘Ransomware’ cyber assault slows as focus turns to catching the hackers who unleashed it
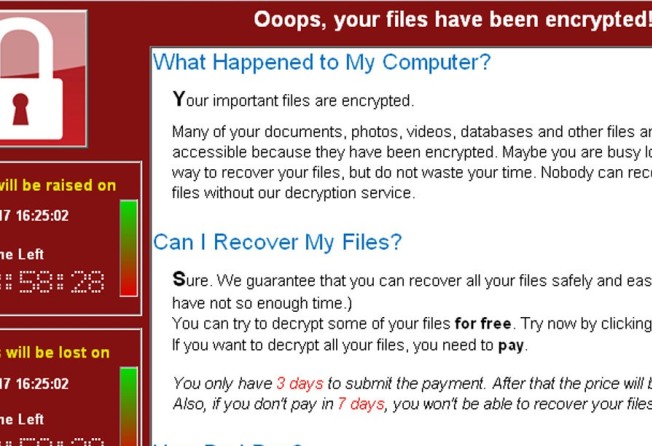
The global WannaCry “ransomware” cyber attack slowed on Monday, with no major infections reported, as global law enforcement agencies shifted their attention to finding the hackers who unleashed it.
The attack infected 300,000 machines in 150 countries, said Tom Bossert, US President Donald Trump’s homeland security adviser. That would make it one of the fastest-spreading campaigns in history.
The US government is investigating whether the attack was launched by cyber criminals or a foreign nation state, Bossert said, noting that the perpetrators had raised less than US$70,000 from users looking to regain access to their computers.

“We are not aware if payments have led to any data recovery,” Bossert said, adding that no federal government systems had been affected.
Private cyber security experts said they were not sure if the motive of the attack was primarily to make money, noting that most large ransomware and other types of cyber extortion campaigns pull in millions of dollars of revenue.
“I believe that this was spread for the purpose of causing as much damage as possible,” said Matthew Hickey, co-founder of British cyber consulting firm Hacker House.
The countries most affected by WannaCry to date are Russia, Taiwan, Ukraine and India, according to Czech security firm Avast.
Stocks of cyber security companies surged as investors bet on governments and corporations spending to upgrade their defences.
Authorities in Europe and the United States turned their attention to preventing hackers from spreading new versions of the virus.
Shares in firms that provide cyber security services rose sharply, led by Israel’s Cyren Ltd and US firm FireEye Inc. Cisco Systems closed up 2.3 per cent, making it the second-biggest gainer in the Dow Jones Industrial Average, as investors focused more on opportunities the attack presented rather than the risk it posed to corporations.
Morgan Stanley, in upgrading the stock, said Cisco should benefit from network spending driven by security needs.
The number of infections has fallen dramatically since Friday’s peak when more than 9,000 computers were being hit per hour. By afternoon on the US East Coast, new infections had fallen to the low hundreds of machines and continue to decline, Avast said.
Earlier on Monday, Chinese traffic police and schools reported they had been targeted as the attack rolled into Asia for the new work week, but no there were no major disruptions.
Beyond the immediate need to shore up computer defences, the attack has turned cyber security into a political topic in Europe and the United States, including discussion of the role national governments play.
In a blog post on Sunday, Microsoft President Brad Smith confirmed what researchers already widely concluded: the attack made use of a hacking tool built by the US National Security Agency (NSA) that had leaked online in April.
He poured fuel on a long-running debate over how government intelligence services should balance their desire to keep software flaws secret - in order to conduct espionage and cyber warfare - against sharing those flaws with technology companies to better secure the internet.
On Monday, Bossert sought to distance the NSA from any blame.
“This was not a tool developed by the NSA to hold ransom data. This was a tool developed by culpable parties, potentially criminals or foreign nation-states, that were put together in such a way as to deliver phishing emails, put it into embedded documents, and cause infection, encryption and locking,” Bossert said.
“Once they’re let out of the lamp, genies of this kind, especially those created by intelligence services, can later do damage to their authors and creators”
Russian President Vladimir Putin, noting the technology’s link to the US spy service, said it should be “discussed immediately on a serious political level.”
“Once they’re let out of the lamp, genies of this kind, especially those created by intelligence services, can later do damage to their authors and creators,” he said.
In Britain, where the virus first raised alarm when it caused hospitals to divert patients on Friday, it gained traction as a political issue just weeks before a general election. The opposition Labour Party accused the Conservative government of leaving the National Health Service (NHS) vulnerable.
“The government’s response has been chaotic,” Labour’s health spokesman Jon Ashworth said. “If you’re not going to allow the NHS to invest in upgrading its IT, then you are going to leave hospitals wide open to this sort of attack.”
Britain’s NHS is the world’s fifth-largest employer. The government says that under a previous Labour administration the trusts that run local hospitals were given responsibility to manage their own computer systems.
Asked if the government had ignored warnings over the NHS being at risk from cyber attack, Prime Minister Theresa May told Sky News: “No. It was clear (that) warnings were given to hospital trusts.”
British health minister Jeremy Hunt said it was “encouraging” that a predicted second spike of attacks had not occurred, but the ransomware was a warning to public and private organisations.

Some victims were ignoring official advice and paying the US$300 ransom demanded by the cyber criminals to unlock their computers, which was due to double to US$600 on Monday for computers hit by Friday’s first wave.
So far only a few victims of the attack appeared to have paid, based on publicly available bitcoin accounts on the web, where victims have been instructed to pay.
This coming Friday, victims face being locked out of their computers permanently if they fail to pay the US$600 ransom, said Tom Robinson, co-founder of Elliptic, a London-based private security company that investigates ransomware attacks.
As of 1400 GMT, the total value of funds paid into anonymous bitcoin wallets the hackers are using stood at just US$55,169, from 209 payments, according to calculations using publicly available data.
Brian Lord, managing director of cyber and technology at cyber security firm PGI, said victims had told him “the customer service provided by the criminals is second-to-none,” with helpful advice on how to pay: “One customer said they actually forgot they were being robbed.”

British media were hailing as a hero a 22-year-old computer security whiz who appeared to have helped stop the attack from spreading by discovering a “kill switch” - an internet address which halted the virus when activated.
Individual European countries and the United States saw infections at a rate of only 10 per cent to 20 per cent of the most affected countries, according to the researcher who stumbled on the “kill switch.”
The virus hit computers running older versions of Microsoft software that had not been recently updated. Microsoft released patches last month and on Friday to fix a vulnerability that allowed the worm to spread across networks.
Infected computers appear to be largely out-of-date devices. Some were machines involved in manufacturing or hospital functions, difficult to patch without disrupting operations.