
Is North Korea behind WannaCry virus?
Putin blames the United States, Edward Snowden blames Russia and the US blames Pyongyang, via the shady Lazarus Group. Here’s the lowdown
North Korea last Sunday fired a missile that went five times higher than the International Space Station – 2,111 kilometers up, to be exact – before returning to earth and landing in the Sea of Japan. That launch has American experts worried for a very particular reason – it proved Pyongyang has the re-entry technology that could one day help it to target the continental United States.
But as the world watches North Korea inch closer to reaching the mainland US with a nuclear warhead, the regime is also developing other means of attack.
On February 13, North Korean leader Kim Jong-un’s half-brother, Kim Jong-nam, was killed in Kuala Lumpur International Airport with VX, the world’s deadliest nerve agent.

While it hasn’t been proved conclusively that North Korea was behind the killing, much of the world believes that to be the case.
And if it was, some experts believe that the killing was meant to serve a message that North Korea can and will hit airports in this way.
Aside from its chemical capabilities, North Korea has also been developing sophisticated means of cyberwarfare.
Mystery of the North Koreans who left Macau for Zhuhai ... where are they now?
Since May 12, more than 300,000 computers in over 150 countries have become infected by WannaCry ransomware, a worm that targets Microsoft Windows systems, encrypts victims’ data and demands bitcoin payments of US$300 within three days or US$600 within six days to release the data. WannaCry uses hacking tools developed by the United States National Security Agency, namely EternalBlue and DoublePulsar, to access victims’ computers. Since individual users are less likely to pay than companies or institutions, whose data are more valuable, WannaCry has been used to target entities such as the Chinese public security bureau, FedEx, the Indian governments of Kerala, West Bengal and Gujarat, Russia’s Ministry of Foreign Affairs and England’s National Health Service. India, Russia, Taiwan and Ukraine have so far been hit hardest.

SHADOW BROKERS
It started last summer when the hacker group known as The Shadow Brokers began auctioning cyberwarfare tools allegedly used by the Equation Group, arguably the most sophisticated hacking toolkit in the world, which is believed to be tied to the NSA. One theory is that Harold T. Martin III, a former contractor for the management consulting firm Booz Allen Hamilton who is accused of stealing 50 terabytes from the NSA, founded The Shadow Brokers.
On August 16, Edward Snowden claimed on Twitter that Russia could be behind the group. But a third theory points to North Korea, since The Shadow Bankers released the EternalBlue exploit in March, which has since been used in the WannaCry ransomware attack.
Three strange links between Macau, North Korea: from Saddam Hussein to customs chief’s death
“A researcher from South Korea’s Hauri Labs said on Tuesday their own findings matched those of Symantec and Kaspersky Lab,” Dustin Volz of Reuters reported on May 14, “who said on Monday that some code in an earlier version of the WannaCry software had also appeared in programs used by the Lazarus Group, identified by some researchers as a North Korea-run hacking operation.”
Russia was quick to deny culpability.
“Microsoft said it directly – the initial source of the virus is the United States security agencies,” Russian President Vladimir Putin said on May 15. “Russia’s got absolutely nothing to do with it.”
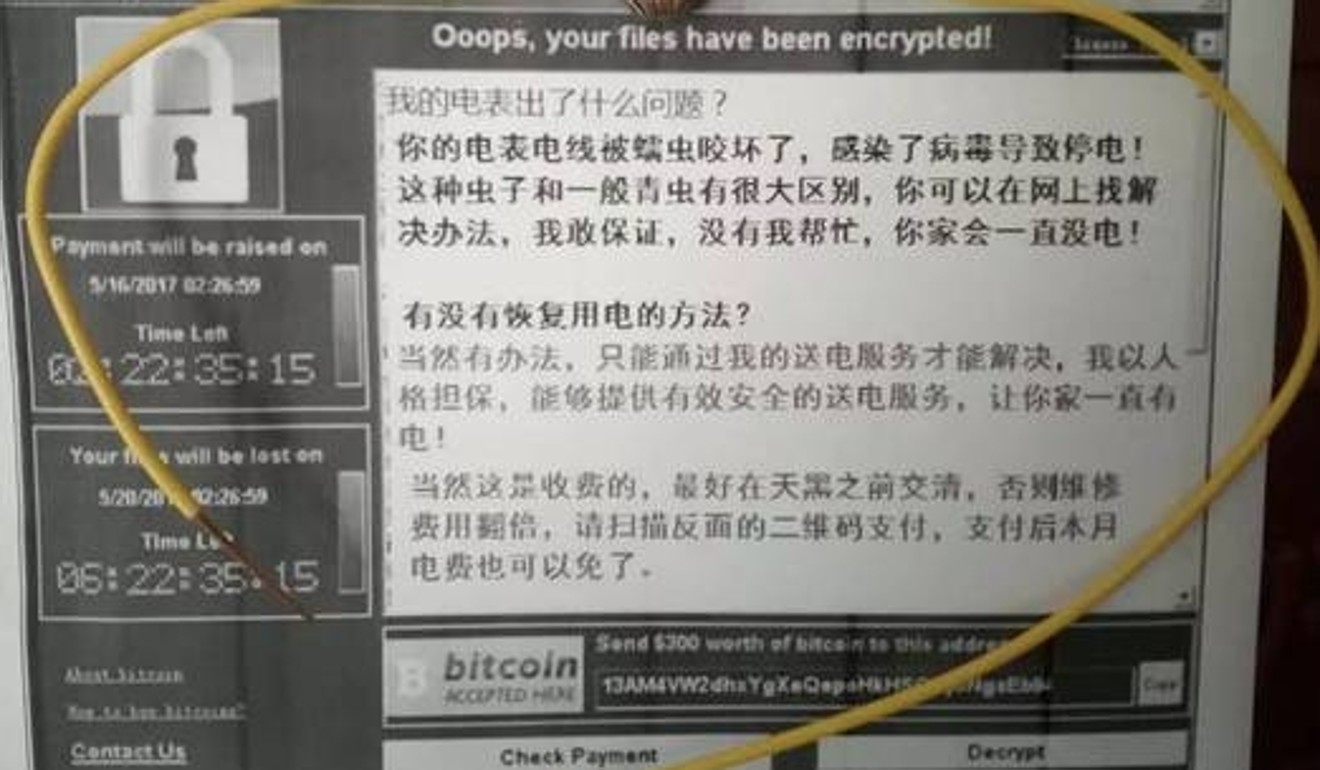
But the fact that it originated in the United States doesn’t necessarily US involvement – after all, The Shadow Brokers claimed to have stolen this instrument and were auctioning it last summer. It seems more likely that someone picked it up, possibly Lazarus Group, which has a history of alleged cyber attacks. The US, for instance, blamed the Lazarus Group for hacking Sony computers before the release of the film The Interview in December 2014. That film featured a scene depicting the assassination of Kim Jong-un in slow motion. Unlike the NSA’s cyber warfare unit, Tailored Access Operations, China’s PLA Unit 61398 or North Korea’s own Office No. 91, Lazarus Group seems less interested in gathering intelligence than disrupting South Korean systems or stealing money.
WATCH: North Korea detains another US citizen
According to Kaspersky Lab, Lazarus Group probably was behind the February 2016 Bangladesh Bank heist, in which US$101 million was stolen from an account at the Federal Reserve Bank of New York that belonged to the central bank of Bangladesh. Since then, US$38 million has been recovered.
How Macau became North Korea’s window to the world... and its nexus for weapons and drugs trafficking
On April 3, Kaspersky Lab released a report directly linking Lazarus Group to North Korea. The group has also been tied to attacks on the South Korean government in 2007, 2009, 2011 and the 2013 DarkSeoul attack, which took out a number of South Korean financial institutes and broadcast agencies.
Of course, all this assumes Lazarus Group is behind these attacks, as opposed to another group going to great lengths to make it look that way. After all, North Korea’s involvement in the Sony hack has never been proven.
But with regard to WannaCry, Kaspersky Lab and Symantec seem convinced that they’ve found Pyongyang’s fingerprints in the code.

